Overview #
Snapt gone!.. Who will balance my traffic? Says hundreds of infuriated customers by Snapt’s decision to terminate its ADC services. “Where do I shift my application delivery?”
Some outcomes are unexpected, but what you can do is swiftly switch to a more competent alternative regarding price, support, and reliability. Migrating from Snapt ADC to Relianoid ADC can be a complex process, especially if you have a large and complex application environment and have no support.
This guide will show you how to gracefully transfer ADC services from Snapt Nova to Relianoid. Find more about Relianoid products here. Relianoid products
Prerequisites #
As a previous user of Snapt, ensure you meet the following prerequisites.
- A Relianoid ADC node must be installed on your PC, bare-metal, virtual environment, or one must have an active ZVNcloud account. Request an evaluation for on-premise deployment.
- One must have access to the Web graphical interface. If you don’t, follow this quick Installation guide.
- At some point, you were using Snapt Nova, Novasense or Aria, but then realized the platform will soon drop it’s support. So, you must be familiar with Snapt concepts.
- One must be able to create a virtual server in the Relianoid load balancer. Here is a quick guide: Layer 4 and Layer 7 Virtual Server Configuration
Basic concepts #
Node: In snapt, a node is a server or a virtual instance that is responsible for handling incoming requests and then routing the request to one of the Backends within a network. With Relianoid, you may deploy a node on-premise or off-premise in cloud platforms like AWS or digital ocean.
Backends: In snapt, backends refer to the servers that host the web application or service being served by the load balancer. The load balancer distributes incoming traffic among the backend servers, allowing the application or service to scale and handle a larger volume of requests. Relianoid uses the same concept of Backends.
WAF: Snapt WAF is a security solution that is designed to protect web applications from attacks such as cross-site scripting (XSS), SQL injection, and other types of cyber threats. The WAF monitors and filters traffic to a web application, blocking requests that contain malicious payloads. Relianoid uses a robust IPDS system for traffic monitoring. The system includes a WAF, DoS protection, RBL policy and blacklists.
Health Checks: Health checks monitor the health and availability of backend servers. These are performed periodically by the load balancer or ADC, and they are used to determine if a backend server is able to accept traffic and process requests. Relianoid uses a set of health check commands called Farmguardian.
Listen Binding: Listen Binding usually associates an IP and Port to a specific service group. This is often done to ensure that requests for a particular service or application are always routed to the correct server or servers. In Relianoid ADC, one may associated a binding IP and port by either creating an LSLB, GSLB or a DSLB Farm.
Live Node health: Snapt Live Node Health refers to the process of tracking the performance, availability, and other metrics of the ADC itself. Monitoring can be used to detect issues with the ADC and to alert administrators to take the action needed. In Relianoid, One can monitor health of Backend servers and the entire network through the dashboard. For advanced analysis, one may check the Monitor module, or analyze Log files.
Example configurations: SSL Termination #
SSL termination is quite useful in environments where there are multiple servers on one load balancer, as it allows the load balancer to offload the SSL processing onto itself. This helps improve the overall performance of the web server cluster by reducing work overload. Besides, SSL termination helps filter out malicious payloads sent by an attacker by performing content filtering on malicious scripts within the request body. To learn more about SSL offloading, read this article: SSL offloading in Relianoid Hardware and Virtual load balancer
In this section, we will demonstrate how one would configure SSL termination in Snapt ADC and use the similar concept later in Relianoid ADC.
Snapt configurations #
We will demonstrate how one would create a new ADC and add SSL Termination to it.
- To create an ADC, one would hovers over the ADCs menu item and then clicks the ADCs submenu item.
- Then scrolls down to the add ADC section.
- We would then click the create button.
- Give the ADC a suitable Name that identifies it.
- Under Choose ADC Type, select SSL Termination.
- Click the Submit button to save the configurations.
- After, we could add a balancing method, session persistence or upload an SSL certificate. For now, we will upload an SSL certificate that we will use for SSL Termination. Under SSL certificates, choose the Uploaded certificates option if you already have one on the ADC, or choose the Let’s encrypt option if you want to create one using the let’s encrypt program.
- Configure the Backends where you want send the traffic.
- One would then customize other settings to add more security features like a WAF, bot control or Geofencing. We will not cover all of these in this section.
- Scroll down and click the Save button.
- With these configurations, one would have created a Snapt ADC with SSL termination enabled. These configurations would enable the load balancer to perform content switching and filtering which is necessary when using a WAF.
Relianoid configurations #
-
- To enable SSL termination in Relianoid ADC, click on the LSLB menu.
- Click on the Farms button.
- Click on an Edit Icon besides a Farm with an HTTPS profile. If you haven’t created a Farm yet, read this guide: Layer 4 and Layer 7 Virtual Server Configuration
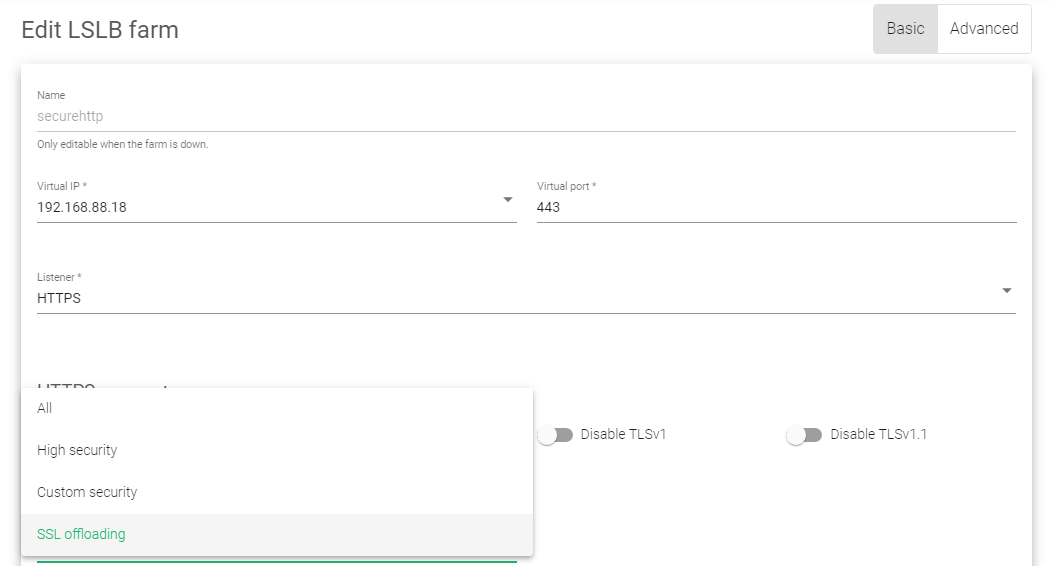
- Ensure the Listener is set to HTTPS and the port in case of a web server to 443.
- Scroll down to the Ciphers section. Change the cipher option from All to SSL Offloading.
- Drag and drop an uploaded SSL certificate from Available certificates to Enabled certificates.
- Under the Actions section in the top right corner, click the Green play button. The Status will change from Red to Green.
To learn more about SSL certificate on Relianoid ADC, read this documentation: LSLB | SSL Certificates
Example configurations: Firewall configuration #
A WAF operates by inspecting incoming traffic to a web application and blocking any requests that do not meet the predetermined security rules. These rules can be based on various criteria, such as the type of request, the source of the request, or the content of the request.
WAFs are important security measures for web applications, as they help to protect against a wide range of threats.
In this section, we will discuss how one would configure Snapt ADC WAF rules and later use those concept to configure XXS detection and protection in Relianoid ADC.
Snapt configurations #
To configure a WAF in Nova, one had a Nova ADC deployed within a Node.
- Within the Nova Dashboard, one would then click on the ADCs menu item.
- Click on the ADCs option within the Drop down menu.
- Scroll down to the add ADC section and choose the one he had configured to manage his website.
- Click on the Edit button along side the ADC of interest.
- Within the page that showed up, he/she navigated to the Performance & Security tab.
- Scroll down till you reach the Security subsection.
- Within the security section, one had to Enable Nova WAF.
- Scroll to the button and click the Save button.
- Snapt would automatically update the configuration of the firewall.
Relianoid configurations #
A WAF in Relianoid ADC works a bit differently, as one is able to customize their rules to suite the needs of their application. We will use these configurations to describe how one can protect their web application against all forms of XSS attacks. However, one may follow this similar procedure to enable SQL injection detection, and mechanisms to other security threats.
To Enable Cross-site scripting detection and protection, you need to create a WAF Ruleset first.
- Go to IPDS >> WAF >> Rulesets on the side menu.
- Click on the Create WAF ruleset button.
- Assign a Name that easily Identifies this ruleset.
- Leave the Copy ruleset field as –No ruleset–.
- Click the Apply button to save the changes.
- Within the global settings, toggle on the Check request body option.
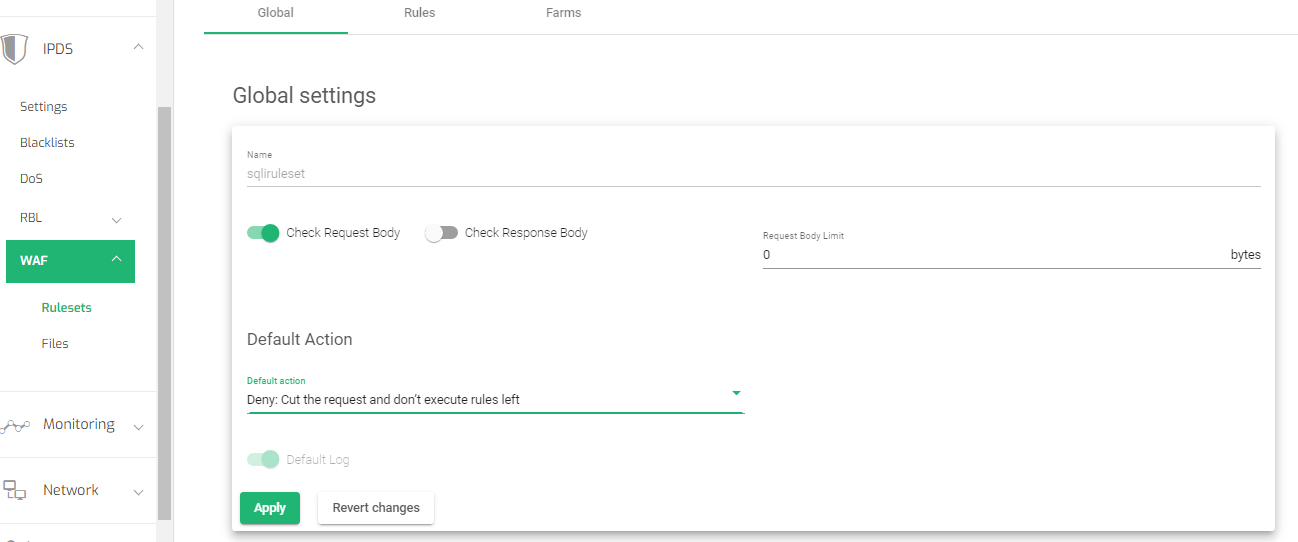
- Change the Default Action to Deny: Cut the request and don’t execute rules left
- Click the Apply button to save the changes.
-
Setting Rules #
- Click on the Rules tab to add new rules.
- Click on the New rule button.
- Select the Rule type as Action.
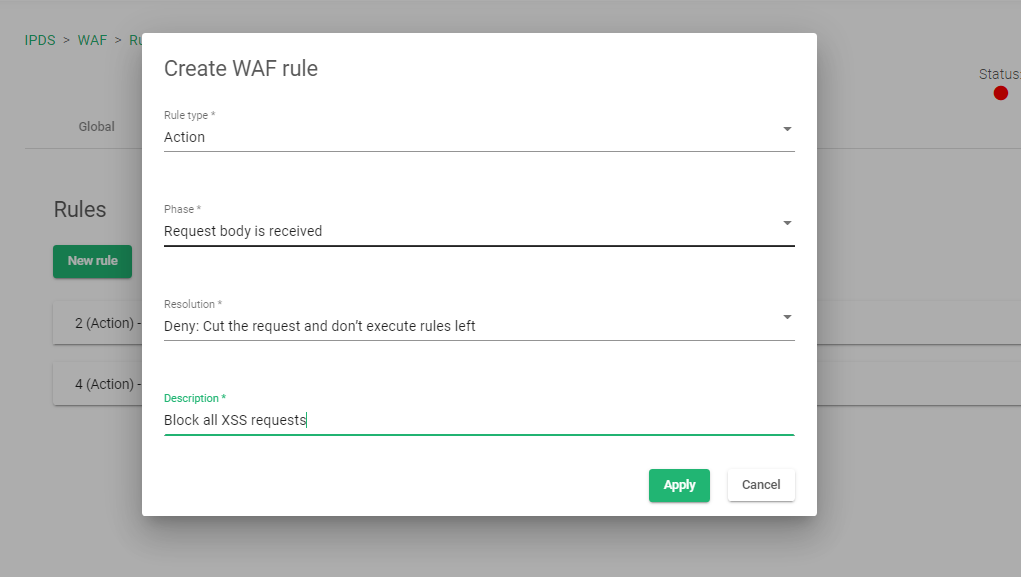
- Select the Phase as Request body received.
- Select the Resolution as Deny: Cut the request and don’t execute rules left.
- Add a description to the rule to easily identify what the rule is all about
- Click the Apply button to save the changes.
-
Adding conditions #
- Click on the Newly created rule to add conditions. Start by clicking on the Create condition button.
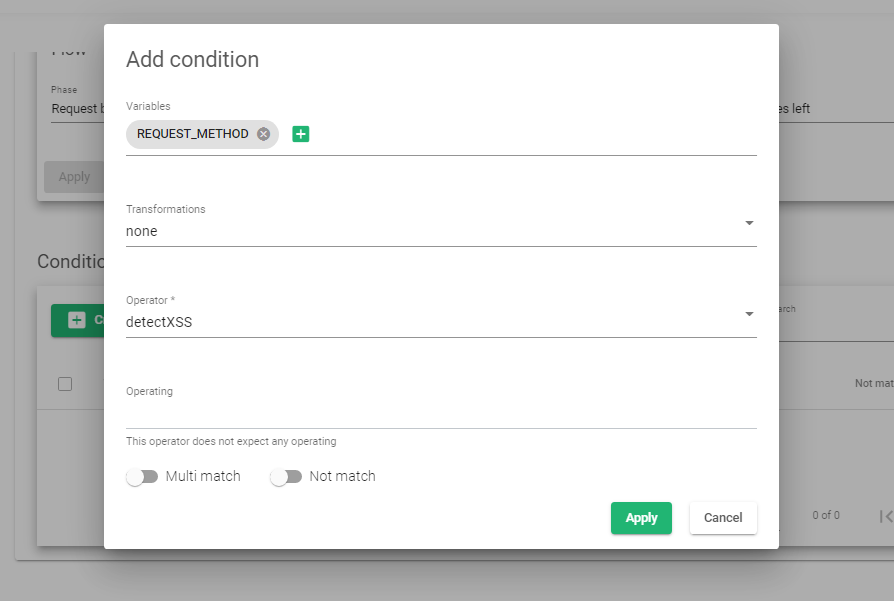
- Within the Variables field, select REQUEST_BODY and click the Add variable button.
- Within the Transformation field, select the option, none.
- Within the Operator section, select detectXSS
- Click the Apply button to create the new condition.
-
Enabling Rules to a Farm #
- Click on the Farms tab to add this rule to a target virtual server(Farm) on the load balancer.
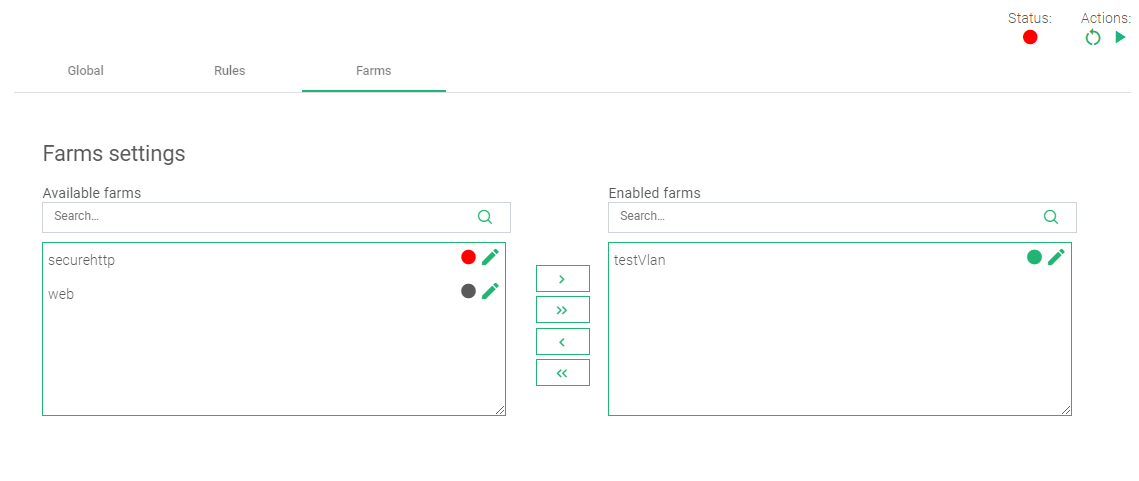
- Within the Farm settings, drag and drop the selected farm from Available farms to Enabled farms.
- In the top right corner, there are Actions. Click the Green play button to start the Rule.
For more resources about the WAF, refer to these articles:
Additional Resources #
Using the Let’s encrypt program to autogenerate an SSL certificate.
Datalink/Uplink load balancing With Relianoid ADC.
Protection from DDoS attacks.
DNS load balancing with GSLB.