Overview #
Let us scale multi-dimensional enterprise-grade systems while maintaining high availability with Relianoid ADC. This means no benchmark limitations on memory, CPU cores, or throughput.
You might have noticed these limitations hindering your network from scaling if you are considering other alternatives besides Kemp. Relianoid Community and Enterprise editions are designed to scale regardless of the deployment platform, whether hardware, Virtual environments, cloud infrastructure, or bare metal.
This article will discuss setting up an instance of Relianoid’s load balancer based on Kemp LoadMaster configurations.
Prerequisites #
To follow this guide, you must:
- Have an active instance of Relianoid ADC on your workstation or a cloud platform. If an instance is not installed, request an evaluation.
- Be familiar with KEMP Loadmaster concepts.
- Have access to the Relianoid web panel. If you don’t, follow this quick installation guide.
- Have knowledge about creating a Virtual server in Relianoid ADC. Follow this guide: Layer 4 and layer 7 virtual server configuration.
Basic concepts #
Virtual service: A virtual service in Kemp’s load balancer is a point of contact from external networks. This interface has a virtual IP and port through which all traffic from the web flows. A virtual service in Kemp’s LoadMaster is the same as a Farm when using Relianoid’s load balancer.
subVS: Use a subVS when segmenting traffic from the WEB and sending it to various requested resources. These resources could be HTML files or download files from FTP servers. A subVS is where you create a pool of backend servers and assign them a role. A subVS is the same as a Service in Relianoid ADC.
Scheduling method: These are methods used when deciding how often clients should access resources from the backend servers. A scheduling method is the same as a Load balancing scheduler in Relianoid ADC.
Real server check methods: Load balancers must monitor the health of nodes serving an application by sending probe signals. These signals check whether a node and its service are healthy. Relianoid ADC uses a set of inbuilt plugins called Farmguardian for health monitoring.
Interfaces: Interfaces are necessary when dividing a local network into various network segments. Network segmentation calls for VLANs. Relianoid load balancer comes with a Network section that allows you to manage different VLANs and assign them IPs through virtual interfaces.
Global balancing: This module provides DNS-level load-balancing schemes. Used when distributing traffic between data centers. The GSLB module does a similar thing in Relianoid ADC, but with more advanced security measures besides enforcing WAF rules.
Real Servers: Real servers are the hosts within a local network. These hosts process all requests from the web and send back a response through a reverse proxy. A real server is the same as a Backend in the Relianoid load balancer.
IPS/IDS: This module provides layer 7 protection when using the Kemp load balancer. It includes a set of WAF rules that protect against any of the top 10 OWASP security attacks. Relianoid uses the IPDS module that provides network security at layers 3, 4, to 7.
Operation: These are commands you give a load balancer to do tasks like creating, editing, deleting, or restarting services. Operations are the same as Actions in the Relianoid load balancer.
Service Type / subVS Type: These options determine whether a service is HTTP or HTTPS. On an HTTP profile in Relianoid ADC, the listener has the protocols, HTTP and HTTPS. The options Service Type and subVS Type are the same as Listeners when using Relianoid ADC.
Pro/protocol: These determine whether a network should transmit UDP or TCP packets. Relianoid ADC has more protocols that cater to layers 4 and 7.
ACME certificates: This protocol automates the interactions between CAs when you need an SSL certificate signed. Relianoid’s load balancer comes with an inbuilt OpenSSL generator with the Let’s Encrypt program.
Example configurations: Content switching #
Websites serve two types of content, dynamic and static. Static content like images, audio, gifs, etc can be accessed directly from databases while dynamic content usually requires more server resources to process based on a user’s behavior. Therefore, we must access these resources differently to maintain high-speed delivery.
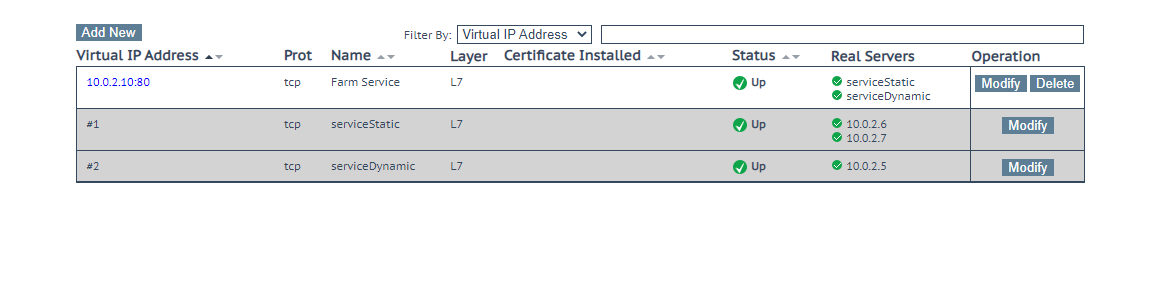
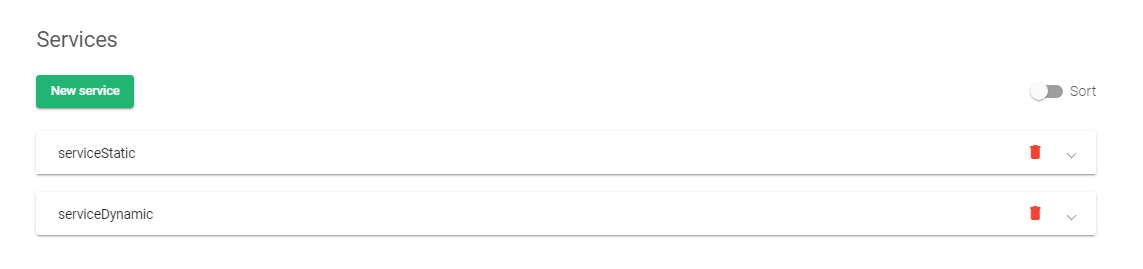
Two service groups must be created on a virtual server. In these example configurations, we shall create the service groups serviceDynamic and serviceStatic to demonstrate content switching with Kemp and how you can achieve that with Relianoid ADC.
Kemp configurations #
- To do content switching, you will need at least two active subVS within a Virtual service.
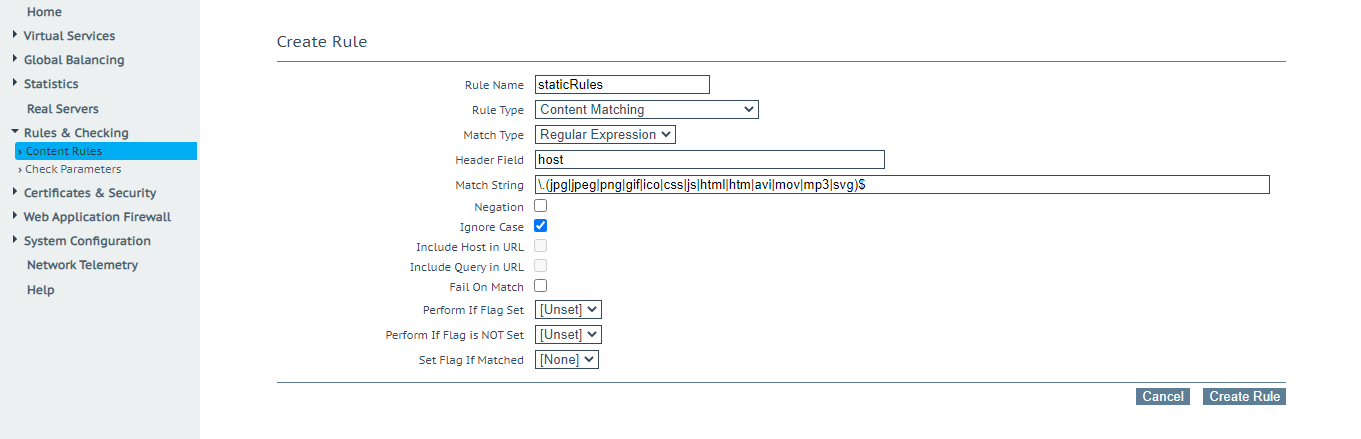
- One must define Content Rules.
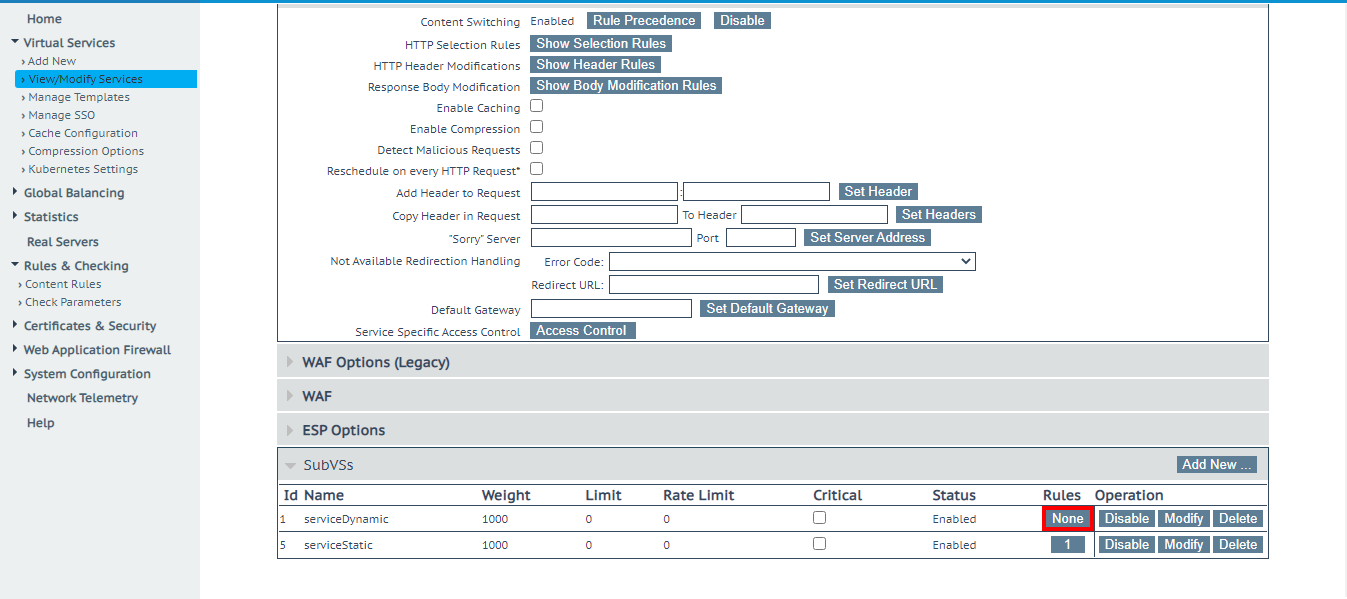
- After creating content rules, enable that rule on a subVS that you want to match. Click the Modify button on a Virtual Service. Scroll till you reach the Advanced properties setting and click the Enable button aside from content switching.
- Scroll to the table at the bottom. Within the column with the heading Rules, click the one with None to add a rule.
- After adding a rule, the status will change from None to 1. For this example, all the traffic that matches this rule will be forwarded to a subVS with static content. All traffic that does match this condition will be forwarded to the subVS with dynamic content.
Relianoid configurations #
- To enable content switching, you will need at least two services on an HTTP Farm.
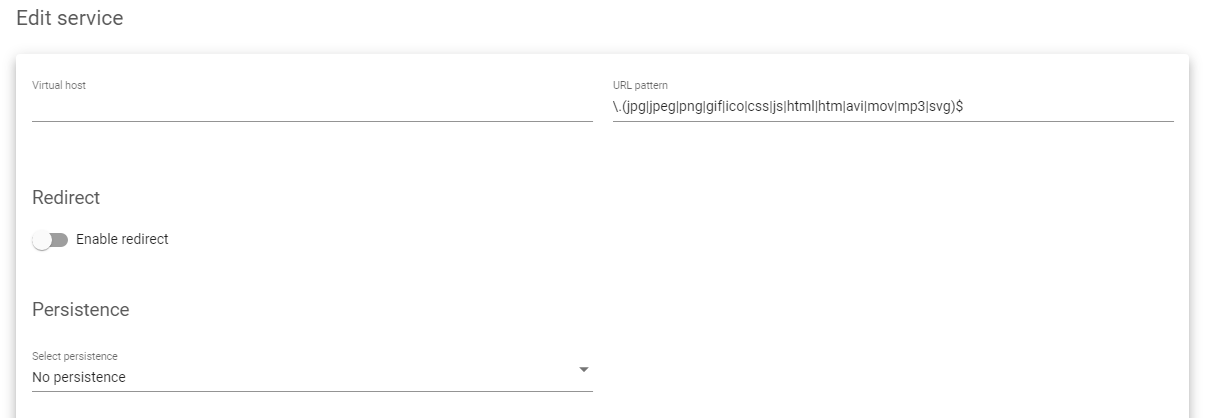
- For this example, we will click and edit the serviceStatic service.
- To load balance on static content, one must use a URL Pattern to match the static files. In this example, we will use the same pattern as with KEMP.
\.(jpg|jpeg|png|gif|ico|css|js|html|htm|avi|mov|mp3|svg)$
- Session persistence is optional. You might leave the field unchanged. However, you must enable health checks. Within Farmguardian, enable http health checks with the flag check_http.
- Save the configurations by clicking the Apply button.
- Create Backends to distribute static resources.
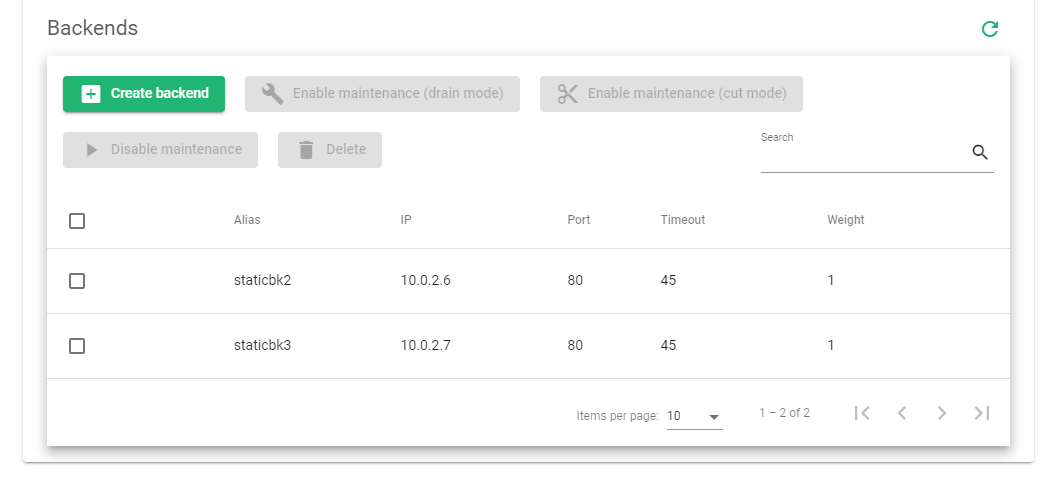
All the traffic from the web that matches the conditional within the URL pattern parameter will get distributed among the listed Backends. Those that do not match will be forwarded to the service serviceDynamic. Make sure to enable session persistence.
Example configurations: SSL Offloading #
SSL offloading can be used to improve the performance of a website by relieving the origin server of the processing burden of encrypting and decrypting traffic. It can also be used to centralize SSL/TLS management and to enable features such as content filtering. When implementing SSL offloading, it is important to ensure that the decrypted traffic is not visible to unauthorized parties and that the traffic is properly encrypted when it leaves the offload device.
In this section, we will show the configurations for setting up SSL offloading on Kemp’s load balancer and how you can achieve the same with Relianoid.
Kemp configurations #
To enable SSL offloading, you must have an ssl cert loaded on the load balancer. This could be one issued by a Certificate Authority or a self-signed certificate.
These are the configurations to enable ssl offloading with the Kemp load balancer.
- Click virtual services on the menu.
- Click view/modify services.
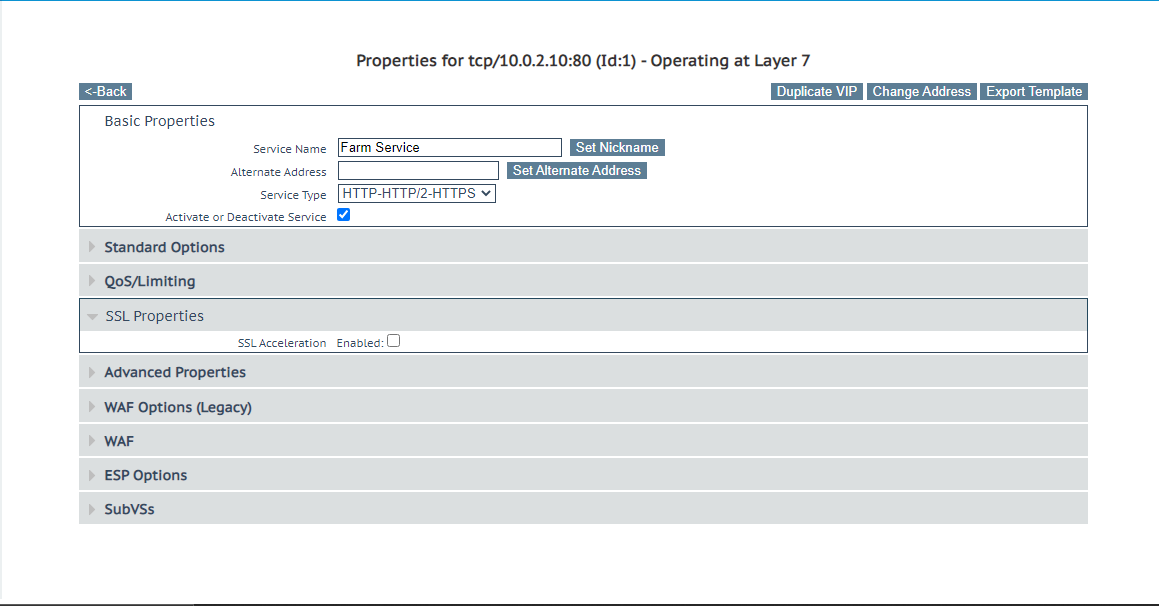
- Click the Modify button under the operations of the selected service.
- Scroll till you reach the SSL properties.
- Enable SSL acceleration.
- Assign the Available certificate in use by shifting it from the Available certificates box to the Assigned Certificates box and click the Set certificates button.
The Kemp load balancer should be able to handle SSL Offloading with this configuration.
Relianoid configurations #
- To enable SSL offloading, go to LSLB
- Click the Farms button.
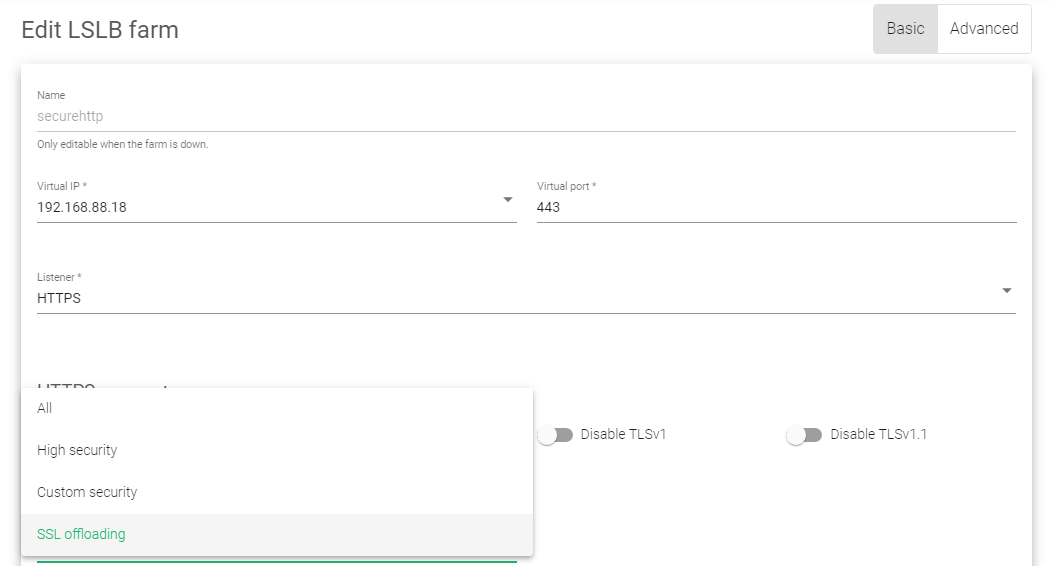
- Click the Edit button on an HTTP or HTTPS Farm.
- Change the listener from HTTP to HTTPS.
- Change the virtual port to 443.
- Under Ciphers, change the option from All to SSL Offloading.
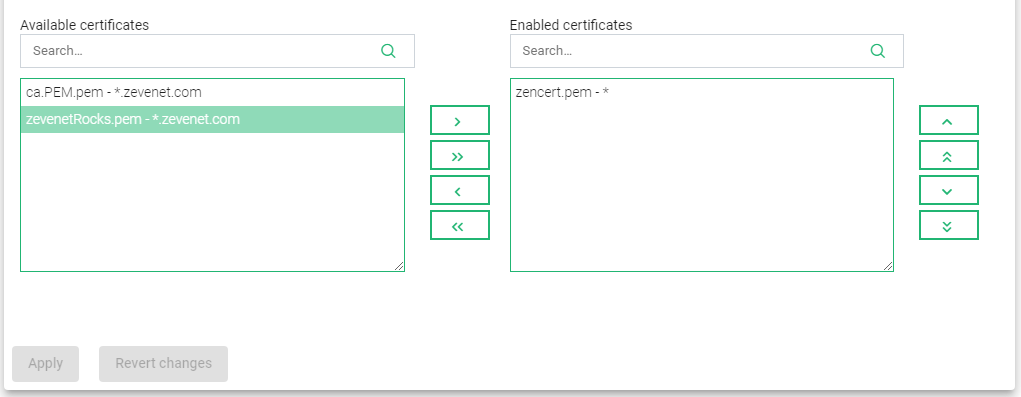
- Click on the Available certificate you want to use.
- Click the greater than Arrow (>) to shift the certificate from Available certificates to Enabled certificates.
- Save the configurations by clicking the Apply button.
- Restart the Farm for the changes to take effect.
Suppose you don’t have an SSL certificate installed on the load balancer, A *.zencert.pem wildcard certificate will be used.
To upload an SSL certificate on Relianoid ADC, read this Article: LSLB | SSL Certificates
To generate an auto ca-signed certificate through the Let’s encrypt program, read this article: LSLB | Let’s Encrypt
Additional Resources #
Using the Let’s encrypt program to autogenerate an SSL certificate.
Datalink/Uplink load balancing With Relianoid ADC.
DNS load balancing with Relianoid ADC.
Protection from DDoS attacks.
Application, Health and Network Monitoring in Relianoid ADC.
Web Application Firewall configuration.
Configuring SSL certificates for the load balancer.